Solution
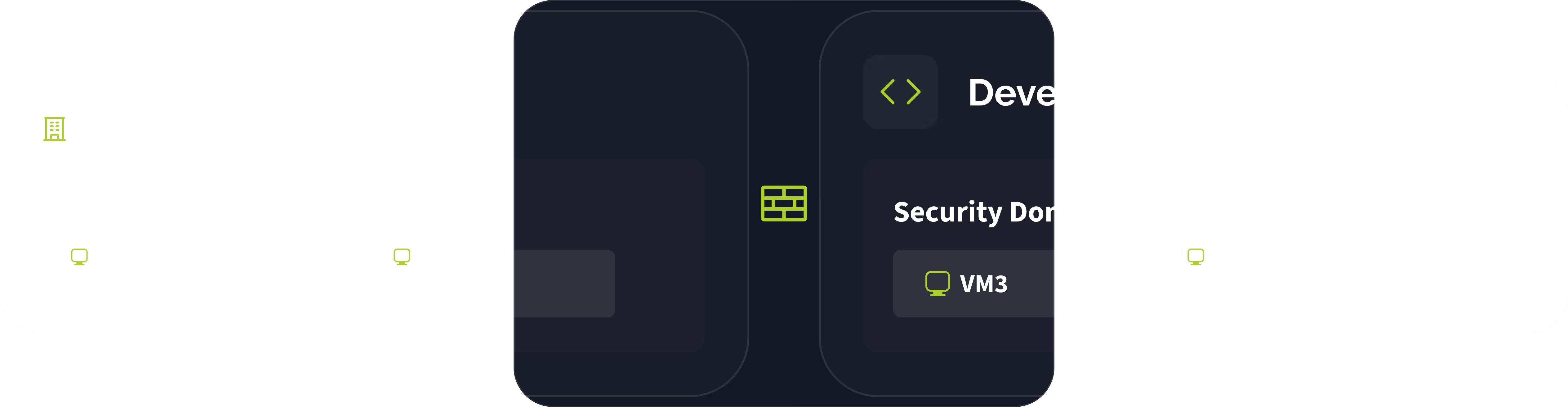
Multiple Security Domains
One Central Command
YS::Desktop gives IT teams a single interface to define, deploy, and manage all security policies across every domain and every endpoint in your fleet.
Central Management
Corporate Domain
VM Windows
USB
VPN
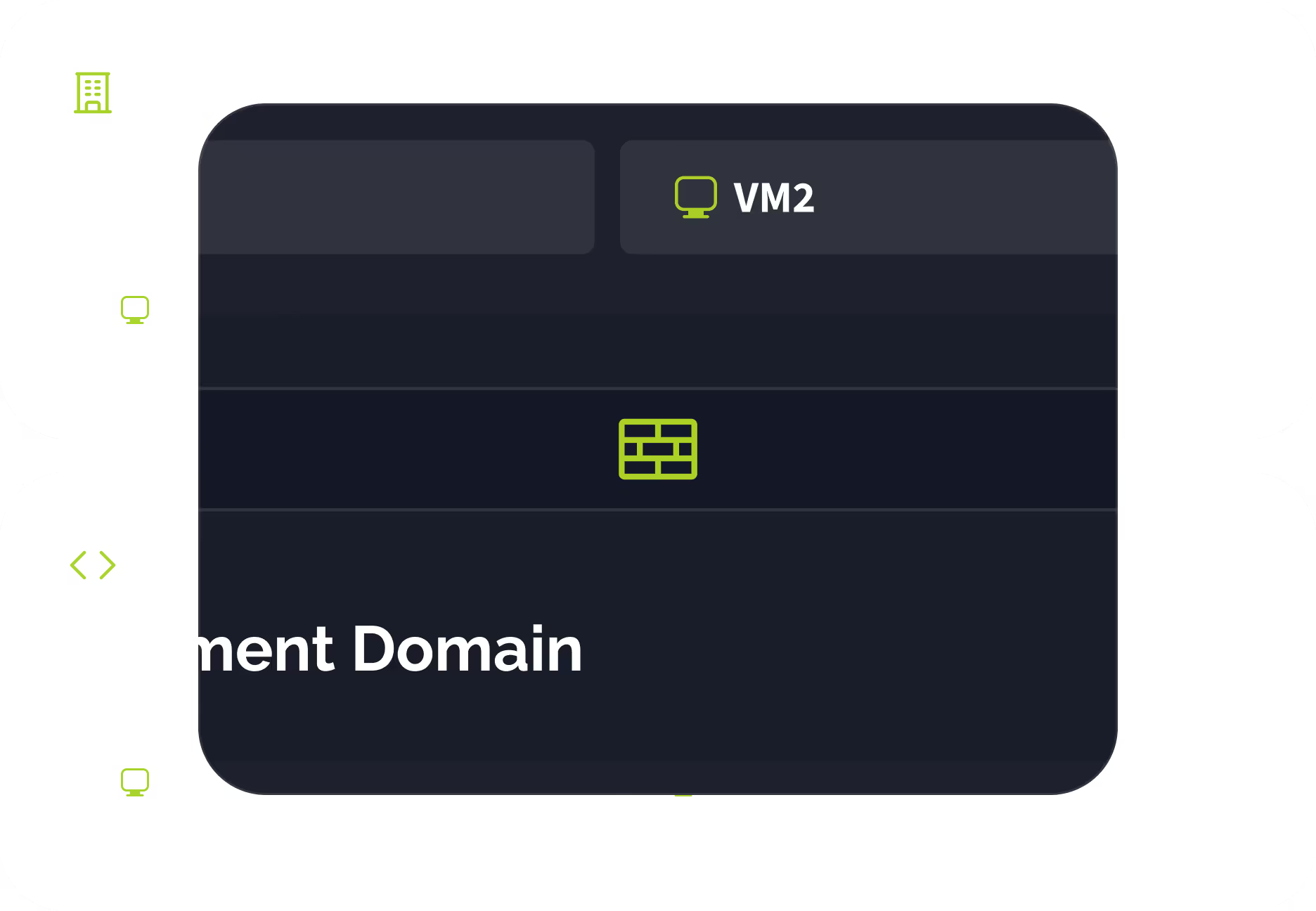
Development Domain
VM Linux
USB
VPN
VM Windows
USB
VPN
VM Linux
USB
VPN
Audit Domain
VM Windows
USB
VPN
Auth
VM Linux
USB
VPN
Auth
Autorized
Blocked
Mandatory
Optionnal
Security Domains: Complete Isolation by Design
Each Security Domain is a strict boundary containing one or more VMs. Everything within a domain belongs exclusively to that domain—no exceptions, no leaks.
What you control
Granular policies that adapt to your security requirements
Device Access Permissions
USB storage, webcams, card readers, and more with granular filtering. Even for composite devices!
Network Access Rules
Cut hardware costs and reduce IT support tickets related to device multiplication.
Pre-authentication Requirements
Optional unlock codes for cryptographic domain protection with an additional secret provided by the user
Network Modes
NAT or Bridge, depending on your architecture needs